OpenSSL buffer overhead
Vulnerability details
A flaw was found in OpenSSL. Calling the OpenSSL API function SSL_select_next_proto with an empty supported client protocols buffer may cause a crash or memory contents to be sent to the peer.
Impacted products
Revisions
| Version |
Date |
Description |
| v1 |
01/20/2025 |
Initial release |
| v2 |
03/27/2025 |
Update and disclose. |

Stormshield Network Security |
CVSS v3.1 Overall Score: 3.4 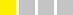
|
Analysis
|
Impacted version
|
|
Affected versions of the SNS firmware are vulnerable to Information Exposure through the SSL_select_next_proto function. This function is typically called from a server side application callback for ALPN or a client side application callback for NPN. This issue has been assessed as Low severity because applications are most likely to be vulnerable if they are using NPN instead of ALPN.
That flaw allows an attacker to cause unexpected application behavior or a crash by exploiting the buffer overread condition when the function is called with a zero-length client list. This issue is only exploitable if the application is misconfigured to use a zero-length server list and mishandles the ‘no overlap’ response in ALPN or uses the output as the opportunistic protocol in NPN. Finally, this issue would not typically be under attacker control, making active exploitation unlikely.
|
- SNS 2.7.0 to 2.7.12
- SNS 3.7.0 to 3.7.42
- SNS 3.11.0 to 3.11.30
- SNS 4.3.0 to 4.3.34
- SNS 4.7.0 to 4.7.10
- SNS 4.8.0 to 4.8.6
|
Workaround solution
|
Solution
|
|
There is no workaround solution.
|
The following SNS versions will fix this vulnerability:
|
| Attack Vector |
Attack Complexity |
Privileges Required |
User Interaction |
Scope |
Confidentiality Impact |
Integrity Impact |
Availability impact |
| Network |
High |
None |
None |
Unchanged |
None |
None |
Low |
| Exploit Code Maturity |
Remediation Level |
Report Confidence |
| Proof of concept code |
Official fix |
Confirmed |
| Confidentiality Requirement (CR) |
Integrity Requirement (IR) |
Availability Requirement (AR) |
| Medium |
Medium |
Medium |